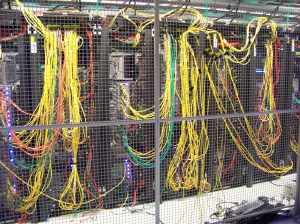
Cabinets prior to re-cabling.

Cabinets after re-cabling.
In a previous post, I listed observations related to server room organization. One of the main sources of clutter in a server room is disorganized cabling. Below are some quick tips to keep your cabling in control. If your server room needs tamed, give JNS a call.
Zipties & Velcro – Use zipties for more permanent cables such as PDU power cables, and structured cabling. Velcro wraps work well for less permanent cabling, for example network cabling from servers to top of rack access switches.
Color Code – Any consistent system will do. One common method is to use a unique color that corresponds to each vlan. Be sure to document the significance of the color, and post in the server room.
Use Custom Cable Lengths – Virtually all cables can be purchased in custom lengths. Power and network cables can both be purchased in 1foot increments. The ultimate in custom length is making your own cables, but the benefit of doing this usually isn’t worth the extra time.
Allow Network Cables to Relax – Network cables are usually sold on a spool or looped in a bag, which gives them a natural tendency to curl. A trick I’ve used is to un-spool the cable and hang it in the hot aisle. The heat and weight of the cable causes the cable to relax and straighten allowing for much faster and neater cable runs. (see photo below for example)

Hang cables for easy storage.
Choose Cable Management Wisely – Avoid using cable management systems that use the smaller, closely spaced, fingers to hold the cable. These systems tend to damage the cable, and make the addition and removal of cable very difficult.
Use an Intuitive System – For instance, one client associated the rack unit of the server, with the port in the top-of-rack access switch. Technicians intuitively expected that the server at rack unit 10 had its NIC connected to port 10 in the access switch. This isn’t possible in all environments, but clever methods to intuitively convey information can help when documentation is lacking.
Separate Inter-Cabinet Cable Runs – The cable runs in the above-cabinet ladder rack are just as important as cabling within the cabinet. Use proper cable management to separate bundles of cables based on the purpose and destination of the cable.




